| Port details on branch 2024Q3 |
- suricata High Performance Network IDS, IPS and Security Monitoring engine
- 7.0.6 security
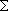 =0 =0      7.0.8Version of this port present on the latest quarterly branch. 7.0.8Version of this port present on the latest quarterly branch. - Maintainer: franco@opnsense.org
 - Port Added: 2024-07-12 17:57:08
- Last Update: 2024-07-12 17:50:07
- Commit Hash: fec84bf
- License: GPLv2
- WWW:
- https://suricata.io
- Description:
- The Suricata Engine is an Open Source Next Generation Intrusion Detection and
Prevention Engine developed by the Open Information Security Foundation (OISF).
This engine is not intended to just replace or emulate the existing tools in
the industry, but will bring new ideas and technologies to the field.
OISF is part of and funded by the Department of Homeland Security's Directorate
for Science and Technology HOST program (Homeland Open Security Technology),
by the Navy's Space and Naval Warfare Systems Command (SPAWAR), as well as
through the very generous support of the members of the OISF Consortium.
More information about the Consortium is available, as well as a list of our
current Consortium Members.
  ¦ ¦  ¦ ¦  ¦ ¦  ¦ ¦ 
- Manual pages:
- FreshPorts has no man page information for this port.
- pkg-plist: as obtained via:
make generate-plist - Dependency lines:
-
- suricata>0:security/suricata
- Conflicts:
- CONFLICTS_INSTALL:
- To install the port:
- cd /usr/ports/security/suricata/ && make install clean
- To add the package, run one of these commands:
- pkg install security/suricata
- pkg install suricata
NOTE: If this package has multiple flavors (see below), then use one of them instead of the name specified above.- PKGNAME: suricata
- Flavors: there is no flavor information for this port.
- distinfo:
- TIMESTAMP = 1720595011
SHA256 (suricata-7.0.6.tar.gz) = 21824f7ff12087c0c9b9de207199a75a9c31b03036688c7cb9c178f0a3b57f8d
SIZE (suricata-7.0.6.tar.gz) = 23644184
Packages (timestamps in pop-ups are UTC):
- Dependencies
- NOTE: FreshPorts displays only information on required and default dependencies. Optional dependencies are not covered.
- Build dependencies:
-
- rustc : lang/rust
- py311-yaml>0 : devel/py-yaml@py311
- gmake>=4.4.1 : devel/gmake
- pkgconf>=1.3.0_1 : devel/pkgconf
- python3.11 : lang/python311
- autoconf>=2.72 : devel/autoconf
- automake>=1.16.5 : devel/automake
- libtoolize : devel/libtool
- Test dependencies:
-
- python3.11 : lang/python311
- Runtime dependencies:
-
- py311-yaml>0 : devel/py-yaml@py311
- python3.11 : lang/python311
- Library dependencies:
-
- libjansson.so : devel/jansson
- liblz4.so : archivers/liblz4
- libnet.so : net/libnet
- libpcre2-8.so : devel/pcre2
- libyaml.so : textproc/libyaml
- libiconv.so : converters/libiconv
- There are no ports dependent upon this port
Configuration Options:- ===> The following configuration options are available for suricata-7.0.6:
GEOIP=off: GeoIP support
HYPERSCAN=off: Hyperscan support
IPFW=on: IPFW and IP Divert support for inline IDP
NETMAP=on: Netmap support for inline IDP
NSS=off: File checksums and SSL/TLS fingerprinting
PORTS_PCAP=off: Use libpcap from ports
PYTHON=on: Python-based update and control utilities
REDIS=off: Redis output support
TESTS=off: Unit tests in suricata binary
====> Scripting: you can only select none or one of them
LUA=off: LUA scripting support
LUAJIT=off: LuaJIT scripting support
===> Use 'make config' to modify these settings
- Options name:
- security_suricata
- USES:
- autoreconf cpe gmake iconv:translit libtool localbase pathfix pkgconfig shebangfix python
- pkg-message:
- For install:
- If you want to run Suricata in IDS mode, add to /etc/rc.conf:
suricata_enable="YES"
suricata_interface="<if>"
NOTE: Declaring suricata_interface is MANDATORY for Suricata in IDS Mode.
However, if you want to run Suricata in Inline IPS Mode in divert(4) mode,
add to /etc/rc.conf:
suricata_enable="YES"
suricata_divertport="8000"
NOTE:
Suricata won't start in IDS mode without an interface configured.
Therefore if you omit suricata_interface from rc.conf, FreeBSD's
rc.d/suricata will automatically try to start Suricata in IPS Mode
(on divert port 8000, by default).
Alternatively, if you want to run Suricata in Inline IPS Mode in high-speed
netmap(4) mode, add to /etc/rc.conf:
suricata_enable="YES"
suricata_netmap="YES"
NOTE:
Suricata requires additional interface settings in the configuration
file to run in netmap(4) mode.
RULES: Suricata IDS/IPS Engine comes without rules by default. You should
add rules by yourself and set an updating strategy. To do so, please visit:
http://www.openinfosecfoundation.org/documentation/rules.html
http://www.openinfosecfoundation.org/documentation/emerging-threats.html
You may want to try BPF in zerocopy mode to test performance improvements:
sysctl -w net.bpf.zerocopy_enable=1
Don't forget to add net.bpf.zerocopy_enable=1 to /etc/sysctl.conf
- Master Sites:
|

 As an Amazon Associate I earn from qualifying purchases.
As an Amazon Associate I earn from qualifying purchases.

 As an Amazon Associate I earn from qualifying purchases.
As an Amazon Associate I earn from qualifying purchases.